Event Bridge Notifications
This pipeline can be used to request and retrieve information about a subscription for the specified notification type, when an event generates a notification to which you are subscribed.
Read more about this end-point here
- NOTE
-
Please fulfil these Prerequisites before configuring the Event Bridge Notifications pipeline:
-
You must have an active Amazon Seller Central Account with permissions to access data you’d like to sync.
-
For Amazon Seller Central, the user being authenticated on DataChannel should either be an Admin or should have view & edit rights on all permissions. These can be assigned to the user through your organisation’s Amazon developer account admin by navigating to Settings → User Permissions. You can read more about managing user permissions here. You can also watch a video Tutorial on How to Invite New Users to Amazon Developer Account
-
Your AWS user should have the following permissions:
-
- EventBridge Permissions
-
Amazon EventBridge permissions in AWS allow you to manage and interact with EventBridge resources, such as event buses, rules, and targets.
-
Event Bus Permissions- These permissions control actions related to EventBridge event buses:
-
events:CreateEventBus– Allows creation of a new custom event bus. -
events:DeleteEventBus– Allows deletion of an existing event bus. -
events:DescribeEventBus– Allows viewing the details of an event bus. -
events:ListEventBuses– Allows listing all event buses within an account. -
events:PutPermission– Allows adding a permission to an event bus policy to grant access to other AWS accounts or services. -
events:RemovePermission– Allows removal of a permission from an event bus policy. -
events:ListTagsForResource– Allows listing tags associated with an event bus. -
events:TagResource– Allows adding tags to an event bus. -
events:UntagResource– Allows removal of tags from an event bus.
-
-
Rule Management Permissions- These permissions control actions related to EventBridge rules, which match events and route them to targets:
-
events:PutRule– Allows creation or update of a rule in EventBridge. -
events:DeleteRule– Allows deletion of a rule from EventBridge. -
events:DescribeRule– Allows viewing details of an existing rule. -
events:DisableRule– Allows disabling a rule, which prevents it from sending events to its targets. -
events:EnableRule– Allows enabling a rule to begin sending events to its targets. -
events:ListRules– Allows listing all rules associated with an event bus.
-
-
Target Management Permissions- These permissions control actions related to EventBridge targets, which receive events when they match a rule:
-
events:PutTargets– Allows adding one or more targets to a rule. -
events:RemoveTargets– Allows removal of one or more targets from a rule. -
events:ListTargetsByRule– Allows listing all targets associated with a specific rule.
-
-
Event Management Permissions- These permissions allow publishing and interacting with events within EventBridge:
-
events:PutEvents– Allows sending custom events to an event bus. -
events:PutPartnerEvents– Allows sending partner events to an event bus. -
events:TestEventPattern– Allows testing an event pattern to determine if it matches a sample event.
-
-
Archive and Replay Permissions- These permissions relate to archiving and replaying events:
-
events:CreateArchive– Allows creation of an archive of events. -
events:DeleteArchive– Allows deletion of an existing archive. -
events:DescribeArchive– Allows viewing details of an archive. -
events:ListArchives– Allows listing all archives associated with an event bus. -
events:StartReplay– Allows starting a replay of archived events. -
events:DescribeReplay– Allows viewing details of an ongoing or completed replay. -
events:CancelReplay– Allows cancellation of an ongoing replay. -
events:ListReplays– Allows listing all replays associated with an event bus.
-
-
Full Access Example Policy- For full access to EventBridge, you would attach a policy like the following:
-
json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "events:*",
"Resource": "*"
}
]
}These permissions cover all necessary actions for managing EventBridge components, such as event buses, rules and targets allowing fine-grained control over who can create, modify, and delete resources.
- CloudWatch Permissions
-
Amazon CloudWatch permissions in AWS allow you to manage and interact with CloudWatch resources in your account.
-
CloudWatch API Operations Permissions- These permissions relate to CloudWatch API operations:
-
cloudwatch:GetMetricData– Required to graph metric data in the CloudWatch console, to retrieve large batches of metric data, and perform metric math on that data.
-
-
- SQS Permissions
-
In AWS, Amazon Simple Queue Service (SQS) provides a set of permissions you can configure for controlling access to your queues.
-
Queue Management Permissions- These permissions control the creation, deletion, and configuration of SQS queues:
-
sqs:CreateQueue– Allows the creation of a new queue. -
sqs:DeleteQueue– Allows the deletion of an existing queue. -
sqs:ListQueues– Allows listing of all SQS queues. -
sqs:TagQueue– Allows adding tags to a queue. -
sqs:UntagQueue– Allows removal of tags from a queue. -
sqs:ListQueueTags– Allows viewing of the tags attached to a queue.
-
-
Queue Access and Message Permissions- These permissions relate to sending, receiving, and managing messages in a queue:
-
sqs:SendMessage– Allows sending messages to a queue. -
sqs:ReceiveMessage– Allows receiving messages from a queue. -
sqs:DeleteMessage– Allows deletion of messages from a queue. -
sqs:ChangeMessageVisibility– Allows changing the visibility timeout of a message. -
sqs:GetQueueAttributes– Allows viewing the attributes of a queue. -
sqs:SetQueueAttributes– Allows modification of a queue’s attributes. -
sqs:GetQueueUrl– Allows retrieval of the URL of a queue based on its name. -
sqs:ListDeadLetterSourceQueues– Allows listing of source queues that have messages destined for a dead-letter queue.
-
-
Permission Management and Access Control- These permissions allow setting and managing permissions for accessing SQS queues:
-
sqs:AddPermission– Allows adding permissions to a queue for specific AWS accounts, granting access to those accounts. -
sqs:RemovePermission– Allows removal of permissions from a queue.
-
-
Monitoring and Debugging Permissions- These permissions are useful for monitoring the activity and operational status of SQS queues:
-
sqs:ListQueueTags– Allows listing of tags associated with a queue, which can be useful for auditing and monitoring. -
sqs:PurgeQueue– Allows purging (deleting all messages) of a queue.
-
-
Policy Permissions- If the SQS queue is controlled by a resource-based policy, you can also define these permissions in the policy itself, which can then be associated with a user or role.
-
Full Access Example Policy- For full access to SQS, you would attach a policy like the following:
-
json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sqs:*",
"Resource": "*"
}
]
}These permissions cover all the essential actions you might need to interact with SQS queues and control access within AWS. Depending on your needs, you can allow or deny specific actions to fine-tune permissions for each user or role.
Configuring the Credentials
Select the account credentials which has access to relevant Amazon Selling Partner API data from the dropdown menu & Click Next
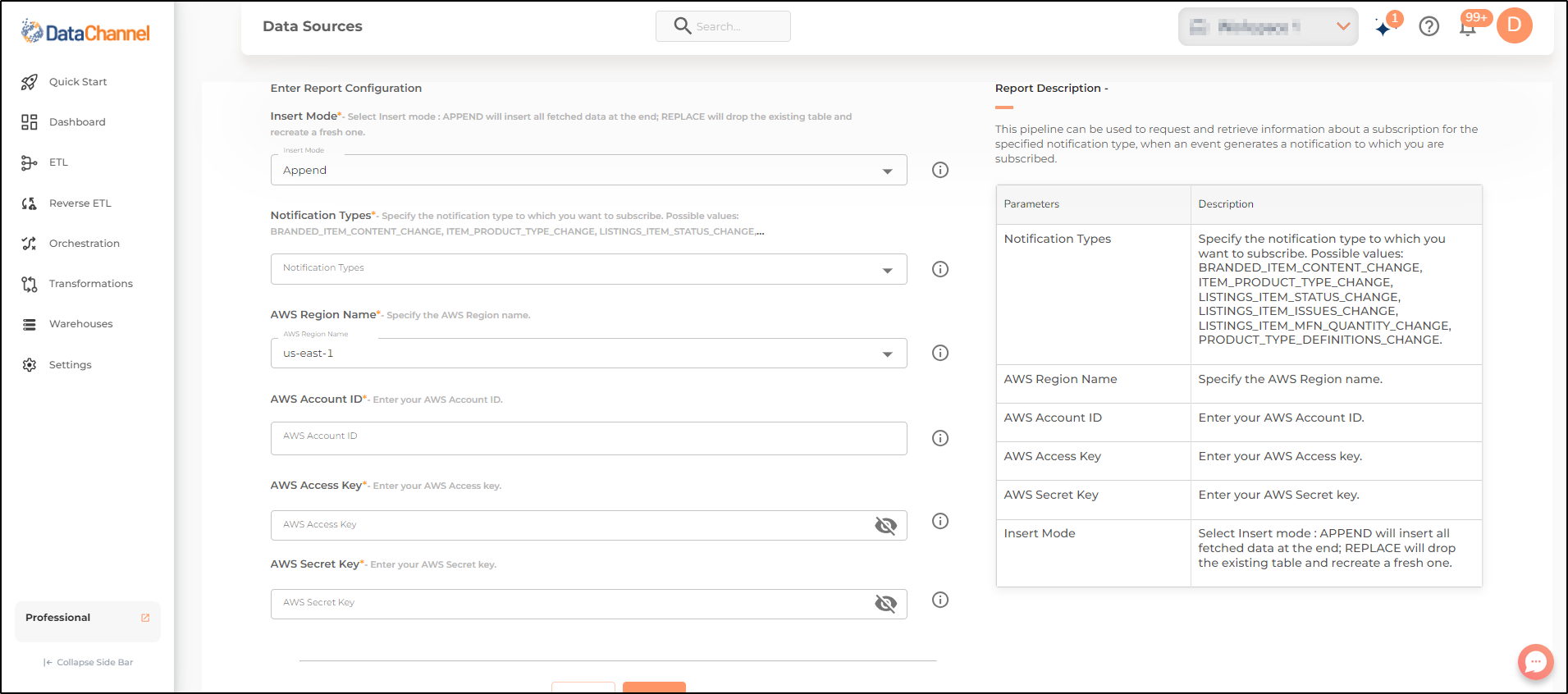
Setting Parameters
| Parameter | Description | Values |
|---|---|---|
Insert Mode |
Optional Specifies the manner in which data will get updated in the data warehouse : APPEND will insert all fetched data at the end, REPLACE will drop the existing table and recreate a fresh one on each run. |
Default Value: Append |
Notification Types |
Required The type of notification to which you want to subscribe. Select from the following notification types: BRANDED_ITEM_CONTENT_CHANGE, ITEM_PRODUCT_TYPE_CHANGE, LISTINGS_ITEM_STATUS_CHANGE, LISTINGS_ITEM_ISSUES_CHANGE, LISTINGS_ITEM_MFN_QUANTITY_CHANGE, PRODUCT_TYPE_DEFINITIONS_CHANGE. Note that Notification type once selected cannot be changed. |
|
AWS Region Name |
Required Specify the AWS Region name. |
AWS Region Name |
AWS Account ID |
Required Enter your AWS Account ID. |
AWS Account ID (String Input) |
AWS ACCESS KEY |
Required Enter your AWS access key ID that identifies your AWS account user. |
AWS ACCESS KEY |
AWS SECRET KEY |
Required Enter your AWS secret key. |
AWS SECRET KEY |
Datapipeline Scheduling
Scheduling specifies the frequency with which data will get updated in the data warehouse. You can choose between Manual Run, Normal Scheduling or Advance Scheduling.
- Manual Run
-
If scheduling is not required, you can use the toggle to run the pipeline manually.
- Normal Scheduling
-
Use the dropdown to select an interval-based hourly, monthly, weekly, or daily frequency.
- Advance Scheduling
-
Set schedules fine-grained at the level of Months, Days, Hours, and Minutes.
Detailed explanation on scheduling of pipelines can be found here
Dataset & Name
- Dataset Name
-
Key in the Dataset Name(also serves as the table name in your data warehouse).Keep in mind, that the name should be unique across the account and the data source. Special characters (except underscore _) and blank spaces are not allowed. It is best to follow a consistent naming scheme for future search to locate the tables.
- Dataset Description
-
Enter a short description (optional) describing the dataset being fetched by this particular pipeline.
- Notifications
-
Choose the events for which you’d like to be notified: whether "ERROR ONLY" or "ERROR AND SUCCESS".
Once you have finished click on Finish to save it. Read more about naming and saving your pipelines including the option to save them as templates here
Still have Questions?
We’ll be happy to help you with any questions you might have! Send us an email at info@datachannel.co.
Subscribe to our Newsletter for latest updates at DataChannel.